A Complete Guide to IT Data Destruction

IT data destruction is a process of destroying the data permanently in such a way that data can never be recovered. All the organizations make use of multiple IT assets during their day-to-day operations. Whether they are hardware assets, software assets or cloud assets all have a significant role in contributing to the organization. These assets undergo different disposition services to be responsibly disposed of at the time of retirement. During disposing the assets, it is very important to clear the data from them in order to maintain data confidentiality. There are different data erasing methods like Data wiping, hardware shredding, degaussing and data destruction.
Data destruction is an important method used only when the assets are not in a condition to be resold or the assets contain sensitive information. The only best option is to destroy the data inside the assets so that it cannot be leaked or misused by any unauthorized person. Improper disposal often leads to heavy fines and penalties as a failure in not following data security and environmental rules. Thus, it becomes important to correctly dispose of the assets and properly erase the data with secure data destruction.
There are different ways of IT data destruction as per the assets type. Software assets are destroyed in a different manner to hardware assets. Different destruction methods are data wiping, degaussing and physical data destruction which includes shredding or crushing. We will have a look at each type of destruction further.
Objectives of IT data destruction:
The primary objective of IT data destruction is data security. Destruction ensures that the data that devices contain must be securely cleared. Confidentiality must be maintained to avoid any cyber threats or consequences. Data security being the primary objective, data destruction also addresses other aspects.
1. Data security:
Proper IT data destruction ensures complete data security. When the assets are at the end of their life, it is very important to properly dispose of them with a secure data destruction to erase the data they contain. If the data is not properly erased it can be easily recovered, increasing the risk of data breach and several cyber risks. As a solution to this risk, destruction serves as a key solution and helps in reducing data breaches.
2. Regular Compliance:
Only erasing the data is not enough but erasing it while maintaining compliance with industry standards like GDPR and HIPPA is essential. Many organizations end up bearing heavy fines and penalties due to a failure in meeting the industry standards. Destruction aims at securely destroying sensitive data with a compliance with data removal and environmental protection laws.
3. Risk Mitigation:
Improper removal of the data can surely result in increasing the risk of data leaks which put organizations at several cyber threat risks. IT data destruction helps organizations mitigate data security and regulatory risks. Additionally, it benefits the organizations to stay risk free and operate smoothly.
4. Environmental responsibility:
Outdated or retired assets are often discarded by the organizations carelessly. These assets end up in increasing the e-waste in the environment. IT Asset Management involves responsible handling of these assets by recycling and refurbishing the assets which reduces e-waste and helps in asset utilization.
5. Cost efficiency:
IT data destruction also helps organizations financially, allowing them to recover some value from their old IT equipment by refurbishing and reselling them in the market. This supports organizations in increasing their cost efficiency and becoming more smart financially.
Read More: The Ultimate Guide to IT Asset Management
The Process of IT Data Destruction:
The process of IT data destruction services involves defined steps that help smoothen the process of destruction and provide complete security and compliance. Let's understand each step one by one:
1. Asset Inventory and Tracking:
The process starts with selecting the assets that are booked for disposition. A list is created for all these assets which contains detailed information such as asset serial number, asset tags and storage capacity. This compete documentation helps in providing proof during audits and enables trusted disposition.
2. Choosing appropriate data erasure technique:
It is very important to choose suitable data erasing techniques for secure and correct data sanitization. IT data destruction services provide best suitable technique to erase the data properly. There are different techniques according to the nature of the assets like secure data wiping for software-based assets and hardware shredding or degaussing for typical hardware assets.
3. Execution:
The selected method is now executed whether its software-based data wiping, hardware-based degaussing or shredding, the methods are executed in such a way that guarantee proper data sanitization that can never be recovered by anyone even with advanced data recovery tools. IT data destruction provider ensures that organizations data remain sensitive and reduces the risk of data breach.
4. Verification:
After the complete data removal process, IT data destruction experts use advance data recovery tools and technologies to cross check no data is left in the device. They check properly before handing over the assets to any secondary buyer and ensure complete data security with compliance.
5. Certification:
A certified IT data destruction company provides proper documentation of the complete process to ensure that everything is effectively operated. They also provide a certificate of destruction (Cod) as a proof of legal data removal. This ensures secure and responsible data destruction while remaining compliant to data security and environmental protection laws.
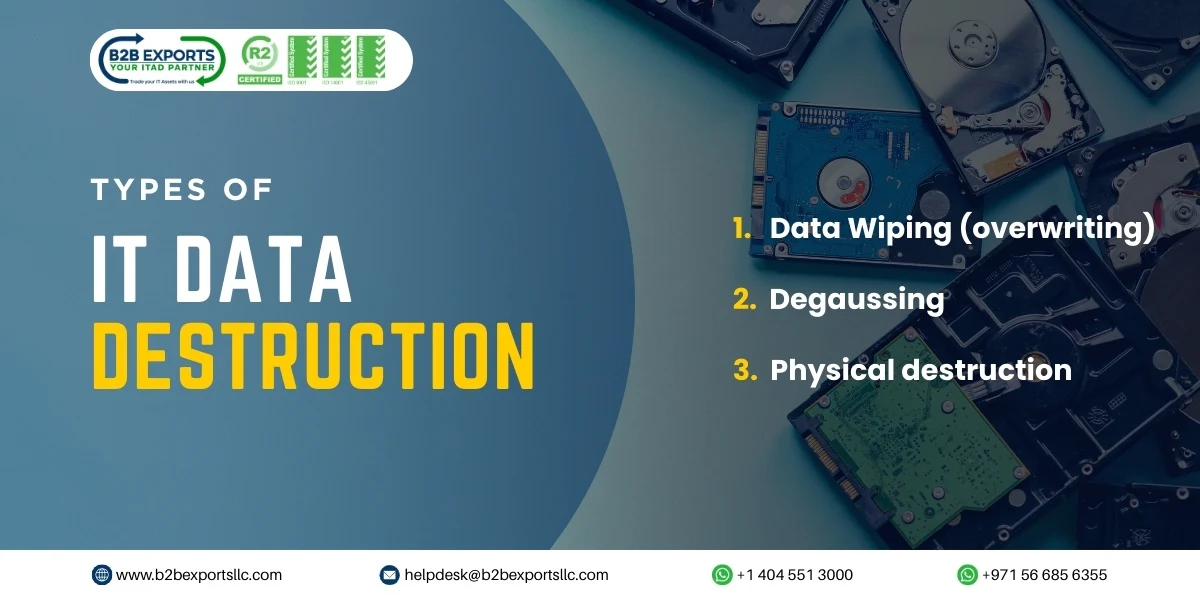
Types of IT data destruction:
There are three main categories of data destruction:
1. Data Wiping (overwriting):
Data wiping is a secure process of permanently removing data from data storage devices. This process involves overwriting new patterns to the existing data repeatedly making the actual data thoroughly overwritten. It meets all the standards like NIST 800-88 and DoD 5220.22-M. This method is best suited for the assets that are still in a good condition to resell.
2. Degaussing:
Degaussing is a method of IT data destruction which uses strong magnetic field to permanently remove the data from magnetic storage devices like HDDs and magnetic tapes making it irrecoverable. It uses a degausser that generates a strong magnetic field to destroy the field used by drivers in the devices. This method is performed to securely erase the data before disposal or destruction of magnetic storage devices.
3. Physical destruction:
IT asset destruction refers to the process of destroying an asset. It involves breaking down of the device into tiny pieces so that it can never be used again and the data inside it becomes irrecoverable. Methods like shredding, crushing and disintegrating the parts can be used to perform destruction. This type of IT data destruction is only brought into action when the organization's data is very sensitive. It helps organizations secure their sensitive data and helps maintain the data confidentiality.
Read More: Complete Guide for IT Asset Disposition
Risks of Improper IT Data Destruction Services:
Improper data destruction services can lead to cause severe problems in the organization. It can result in data breach, heavy fines and penalties and reputational damage.
1. Data breaches and cybercrime:
When organizations lack proper data destruction, data breaches and cybercrime risks increase. Data can be used by unauthorized person, competitors and increase the risk of malicious activities in an organization.
2. Legal and financial penalties:
Without proper IT data destruction services organizations might not be able to erase the data responsibly in compliance with industry standards which increases the risk of several legal and financial penalties.
3. Reputational damage:
Multiple data leaks and legal fines can result in damaging organizations' reputation and loss of trust in the industry. Additionally, it will result in damaging the brand value and degrading its overall image in the market.
4. Loss of competitive advantage:
Competitors can misuse the leaked information to defame your organization and get ahead of you. It can result in lowering your position in the market and degradation of the organization.
5. Environmental hazards:
Improper disposal of the assets also affects the environment. When assets are not responsibly disposed of, several components end up staying in the landfills, harming the environment. Additionally, organizations face multiple fines due to failure in following environmental protection law.
ISO standards for IT data destruction:
An experienced IT data destruction company follows International Certifications & Standards for IT asset data destruction process, to ensure security and compliance at the same time.
1. ISO 27001:
It is an Internationally recognized standard for Information Security Management System (ISMS). It helps organizations to increase their security management system and maintain confidentiality. It is a blueprint for organizations to reduce and manage information security risk.
2. ISO 27040:
It is an ISO standard that helps in providing technical guidance on information security for storage devices. It deals with planning, designing, documentation and implementation of storage security including the security of devices, media and user access. This standard helps organizations mitigate risks associated with their storage environments and ensure confidentiality.
3. ISO 21964:
It is an international standard that defines the security requirements for the destruction of data storage devices such as laptops, desktops, hard drives and other devices. This standard defines different protection classes, materials categories and security levels to ensure proper and correct destruction of sensitive data.
4. ISO 14001:
It is an international standard that defines the requirements for an effective environmental; management system. This standard provides structure to organizations for improving their environmental management performance. It helps an organization to follow proper IT data destruction services that align with environmental protection rules and be a responsible entity in the industry.